Vintage Encryption and Data Security Concept with Combination Puzzle Box or Cryptex with Secret Message Inside Stock Photo - Image of decode, compartment: 246399488

Here's a simple introduction on how browsers encrypt your data | by Anton Spaans | Digital Products Tech Tales | Medium

Block Design including the encryption (red box) and decryption (blue... | Download Scientific Diagram
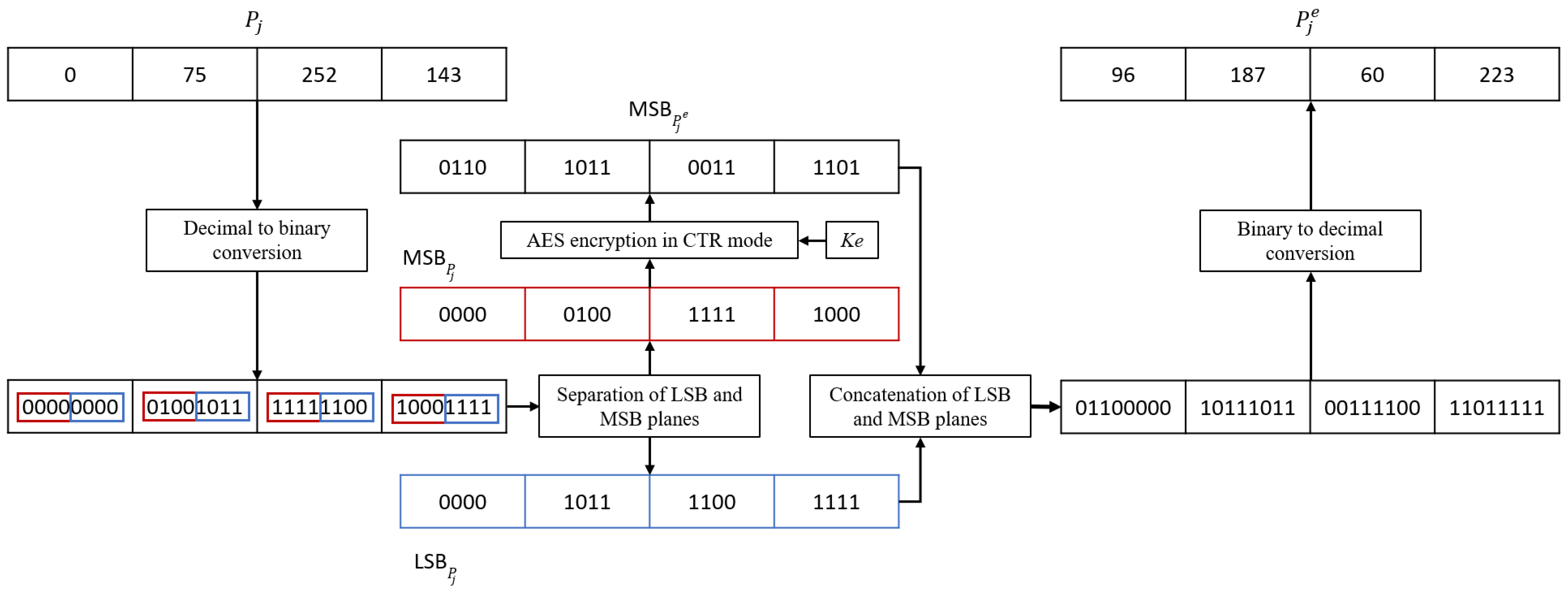
Mathematics | Free Full-Text | Complete Separable Reversible Data Hiding for Encrypted Digital Images Using Code Division Multiplexing with Versatile Bit Depth Management
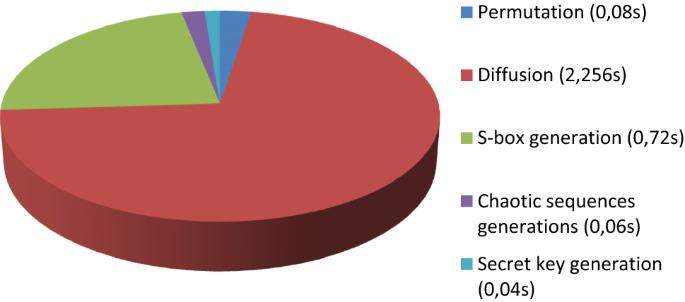
A Novel Image Encryption Scheme Combining a Dynamic S-Box Generator and a New Chaotic Oscillator with Hidden Behavior | SpringerLink

Same DB prior (left) and after softoken password setting: encryption.... | Download Scientific Diagram